
Managed SOC
According to SANS: “A SOC is a combination of people, processes, and technology protecting the information systems of an organization through: proactive design and configuration, ongoing monitoring of system state, detection of unintended actions or undesirable state, and minimizing damage from unwanted effects.”
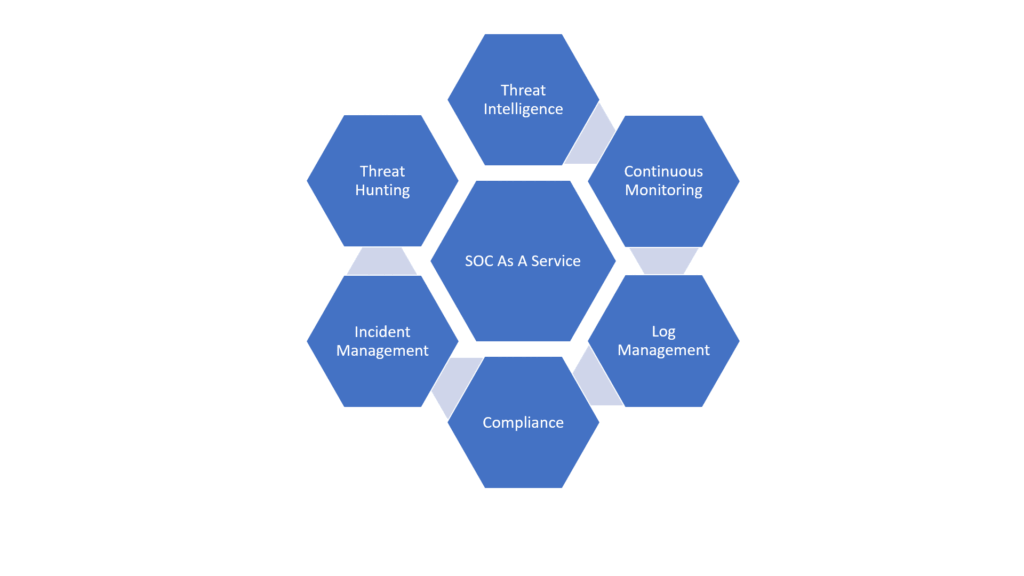
Vsecant provides 24/7 operations using analytic solutions like a SIEM, SOAR, EDR. Our SOC team monitors entire environment including devices, networks, applications, clouds. These tools gather information, aggregate the data, automate the incident response.
SOCs typically utilize security information and event management (SIEM) systems and intrusion detection and prevention systems (IDPS) to monitor and respond to incidents.
Our SOC uses external feeds, data analytics and threat reports to gain insight into motives & behaviors of hackers. With this threat intelligence information, the SOC can uncover threats and fortify the organization against emerging threats.
Log management system collects, maintains, analyzes the log data produced by endpoint, operating system, virtual machine, network event. Our incident response teams limit the damage to the organization.
As part of best practices, we compare the audit results against the NIST CSF. In addition we also validate industry specific or business activity related regulations. While we comply with HIPAA, PCI, we ensure to map your security strategies, operational processes, and technical specifications that meet all of your organizations’ varying requirements. We conduct periodic SOC audits and gap assessments outlined in cybersecurity framework and operate as intended.

Identification
Protection
Detection
Response
Recovery
Our best practices:
- Up-to-Date Cyberthreat Intelligence:
- Staying informed about the latest cyber threats is essential for a SOC. This knowledge enables proactive threat detection and response.
- Scanning, Monitoring, and Testing Tools:
- Our SOC teams rely on a suite of tools to scan networks, monitor activities, and conduct testing. These tools help in identifying vulnerabilities and potential threats.
- Preemptive Addressing of Weak Points:
- Identifying and addressing vulnerabilities in advance is a proactive approach to neutralize potential threats before they are exploited.
- Minimizing Incidents Requiring Active Response:
- Effective prevention and early detection measures can reduce the number of incidents that necessitate an active response, lowering the overall risk.
- Penetration Testing:
- Simulating cyberattacks through penetration testing is a critical step in identifying entry points and vulnerabilities in your systems.
- Analyzing Test Results and Gap Assessments:
- After penetration testing, thorough analysis of results helps SOC teams understand weaknesses and prioritize security improvements.
- Simulating Cyberattack Response:
- Tabletop incident exercises provide valuable opportunities to practice and refine incident response plans and assess team knowledge.
- Enhancing SOC Team’s Knowledge of Policies and Processes:
- Effective training and exercises ensure that SOC team members are well-versed in the organization’s cybersecurity policies and procedures.
In summary, a Security Operations Center’s effectiveness relies on a combination of proactive measures, up-to-date threat intelligence, and regular testing and training. By implementing these best practices, organizations can better protect their systems and data from cyber threats and respond more effectively when incidents do occur.